Alarm Standards
The key values that drive alarm system performance are where the alarm limits are set. Alarm standards recognize this importance, and direct that ‘they should be put at the boundary of where you normally operate’. This was the only advice you ever had for correctly positioning alarm limits. It sounded easy but then you found it was actually very difficult, if not impossible in practice to define the boundary on several hundred process variables corresponding to operating objectives defining ‘normal operation’ specified on maybe only 10 or 20 lab, quality, KPI, performance and equipment constraint variables. You will be relieved to know that PPCL’s C Visual Explorer (CVE) makes it easy to use envelopes of 1,000 or even more variables so that, for the first time ever, you can see a ‘feed to product’ envelope spanning several process units and gain new knowledge of what process activities in which unit lead to you meeting or missing end-of-line targets, KPIs and specifications.
How do you get from limits on ‘result’ (dependent) variables to limits on process (independent) variables? It’s not easy, even if you have a sophisticated first principles process model because process models are almost always in the form of y=f(x) where the y’s are the results and the x’s are the independent variables. You really want a model that gives you x=f(y), but such models don’t generally exist even for simple examples, let alone for the general case of a large operating plant. You could run many cases of a y=f(x) model to populate a solution space as in our paper, but it is generally only practical to do this with a very small model. See Brooks, Drury and van Walsem, Choosing Cut Points to Optimise Product Yields, Hydrocarbon Processing 1999, 78(11), 53-60).
But although algebra can’t deliver, geometry can so that you can see x as a function of y! That’s why CVE’s novel visualization method is such an important discovery. It can combine the dependent and independent variables from process history data into one picture and, by putting the operating objectives and specifications that define ‘normal’ on the dependent y-variables, CVE will show you the actual envelope that you would have used on the independent x-variables to achieve those specifications, targets and KPIs on the y-variables. Or put operating limits on some or all of the independent x-variables and it will show you all the results you would have obtained on the dependent y-variables from which you can immediately calculate the yield of desired results that you would have achieved and decide whether it is better or worse than you are achieving now.
And in the next 5 minutes you can make up ‘better’ and ‘worse’ specifications and add those to the picture so that you have a ‘simple response surface visualization’ or ‘contour map’ to help you understand which independent variable changes will improve or worsen the yield.
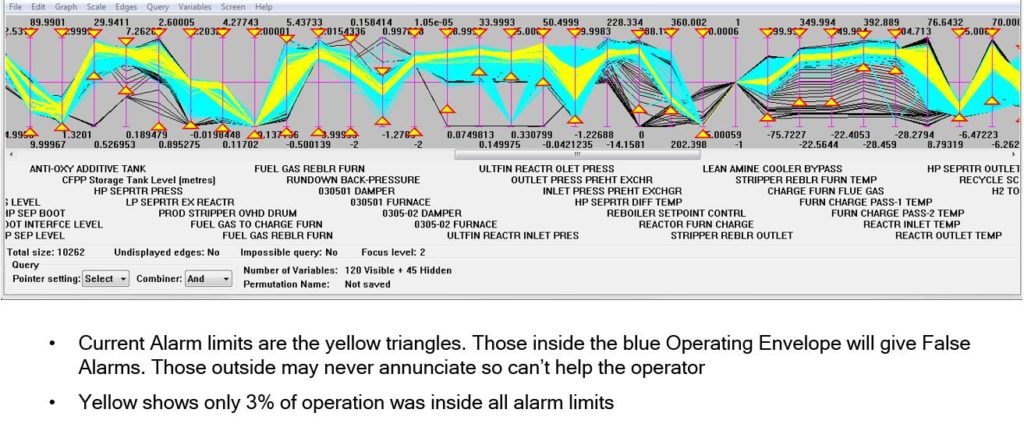
In this CVE plot you are actually looking at Operating Envelopes of your process, so choose the best one and now position your alarm limits on its boundary so that the operator receives an alarm whenever operation strays outside the Operating Window enclosing the Operating Envelope. Set your process controls to keep the process operating inside the consistent Window that they can now have knowledge of for the first time and you will achieve operation with far fewer alarms than ever before and almost no ‘false alarms’.
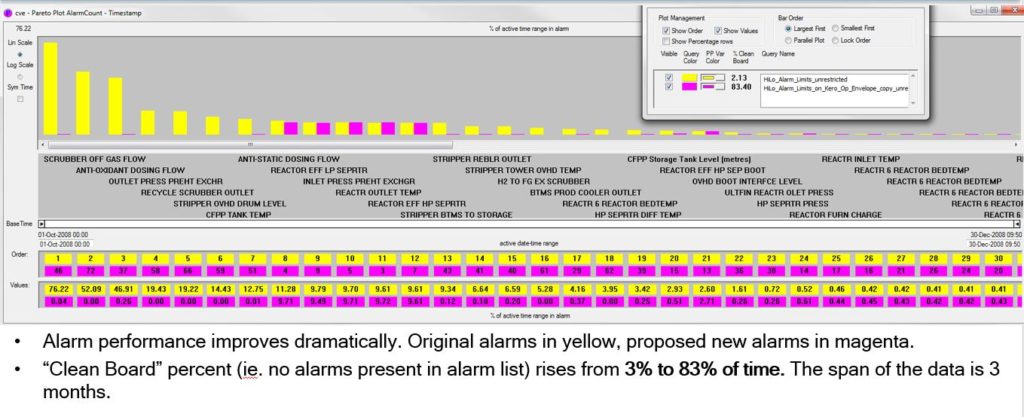
You will achieve ‘Clean Board’ percentages (no alarms on the operator’s alarm list display) greater than 90% and leave the EEMUA 191 Alarm Performance Guidelines trailing in the dust. We also provide a real-time ‘operating envelope controller’ to police the boundary for you and show the operator on a new operator display where he is within the envelope right now and how much space he has to play with.
And you can do all this in far fewer man-hours than you used to need for Alarm Rationalization and with almost none of those interminable meetings while exceeding the requirements of the ISA SP18.2 and IEC 62682 standards. You will still assemble the full team to review the results of the CVE rationalization, but just for a few days instead of several weeks.
